Data does not move by itself; people move data.
This statement may seem simple, but it contains an important insight into data security: technology is only part of the solution. For robust information security, a proper balance is needed between technology that aligns with your organization and employees who know how to handle data securely. In this blog, I’ll share three practical tips to structurally strengthen the human aspect of data security, based on experience in various projects.
1. Form a Diverse Working Group
For your data security initiative, assemble a working group with people from different departments, roles, and backgrounds. Include data owners, department heads, the Chief Information Security Officer (CISO), and representatives from the Central Data Office (CDO), information security, and Document Information Management. This provides insight into information and information flows within your organization. Additionally, expand the group with representatives from IT and functional support.
After all, these are the people that have the real insight on what data is sensitive to your company, and what the specifications or properties of that data are.
2. Make End Users Part of the Design
Automatic detection of sensitive data and targeted alerts for risky actions help raise awareness among end users and support the adoption of data security. However, successful implementation depends on involving users. Start with training that strengthens both knowledge and desired behavior.
Apply a continuous approach: provide regular updates, short microlearning modules, and current threat information to keep data security top of mind. Use gamification and dashboards to increase engagement and make progress visible. This way, data security becomes part of daily work.
If end users are not actively involved, attention often fades quickly after the initial rollout. Without regular updates and awareness, data security slips out of sight, making measures less effective and the organization vulnerable again. Therefore, design a clear adoption strategy for end users. This is just as important as the technical design to ensure lasting data security.
3. Design an Organization-Specific Growth Model
Work with the working group to determine which data within the organization is considered sensitive and map the associated characteristics. In the context of data security, these characteristics are referred to as “sensitive information types” or “SITs”. Identifying these types is essential to support users, as the system can then automatically recognize sensitive data and provide targeted assistance.
Develop a growth model tailored to the organization so that automatic recognition of sensitive data is gradually integrated, reducing the efforts for manual classification over time. Divide the growth model into clear steps and roll out automatic recognition in phases, so employees receive increasing support.
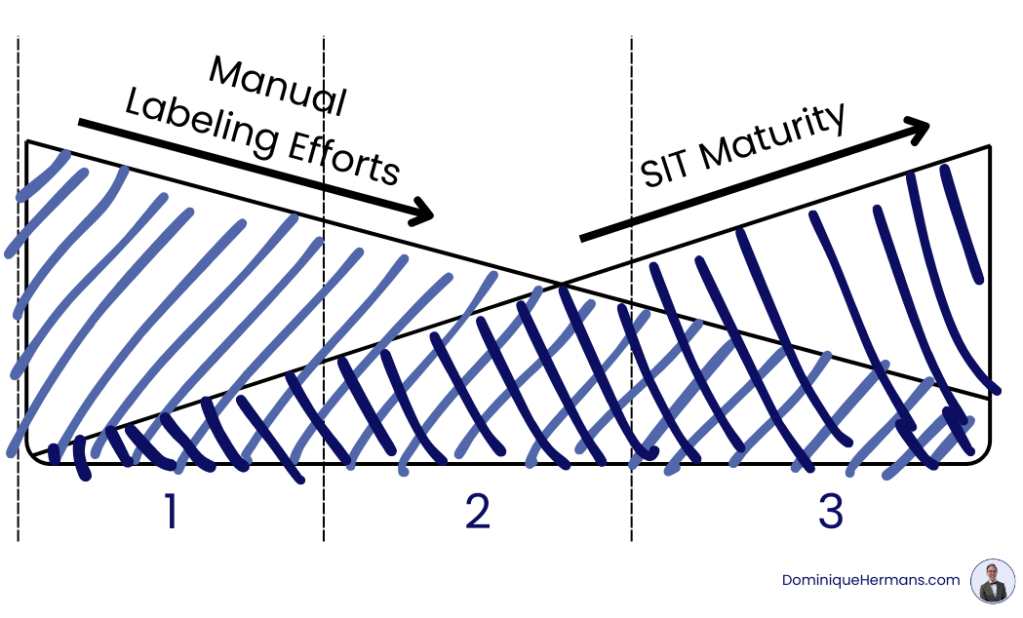
Step 1: Start with an Initial Version of Sensitive Information Types
Use this feature to guide users in classifying information by providing policy tips and classification recommendations based on detected sensitive data. This approach gives your working group time to fine-tune information types while still offering immediate, actionable guidance to users.
Even more importantly, it delivers valuable feedback on how your Sensitive Information Types (SITs) perform in real-world scenarios. Think of it like Spotify: the more you listen, the better its recommendations become, thanks to insights from users with similar tastes. In this case, you’re Spotify, collecting input from users to continuously improve your SITs.
Take, for example, a Dutch license plate. Because you have involved subject matter experts for this type of data in your working group, you already know at the start that Dutch license plates consist of three sections of letters or digits, separated by a hyphen.
Subsequently, based on the feedback received, you discover for example that Dutch license plates never contain vowels. This is therefore the first step in optimizing your SIT.
Proceed to the next step when your organization is ready. The criteria for assessing this step as successful should be defined by your working group. Use, for example, logging and monitoring with feedback from the working group and other stakeholders as sources for your criteria.
Step 2: Implement a Second Version for Automatic Classification
Enable automatic classification when documents containing sensitive data are created or edited. In Purview, this is also referred to as ‘client auto labeling’. Train users and emphasize that they remain ultimately responsible for correct classification.
To further optimize your SITs, in our example we discover that Dutch license plates always have a yellow background with on the left of the license plate, an EU-logo consisting of 12 stars.
Step 3: Optimize and Fully Automate
Further refine sensitive information types and ensure automatic classification (In Purview: ‘service auto-labeling’) is properly configured and verified to have been applied to all existing content.
Finally, continue to monitor logging combined with feedback from the organization, as data and its characteristics are constantly evolving.
In summary
Effective data security requires more than technology, it depends on engaging people and processes. Involve diverse stakeholders, actively include end users in design and adoption, and implement an organization-specific growth model for sensitive data classification. Continuous training, feedback, and phased automation ensure lasting security and adaptability.
Have a nice day!